
Computer systems that are physically isolated from the outside world (air-gapped) can still be attacked. This is demonstrated by IT security experts of the Karlsruhe Institute of Technology (KIT) in the LaserShark project. They show that data can be transmitted to light-emitting diodes of regular office devices using a directed laser. With this, attackers can secretly communicate with air-gapped computer systems over distances of several meters. In addition to conventional information and communication technology security, critical IT systems need to be protected optically as well.
Hackers attack computers with lasers. This sounds like a scene from the latest James Bond movie, but it actually is possible in reality. Early December 2021, researchers of KIT, TU Braunschweig, and TU Berlin presented the LaserShark attack at the 37th Annual Computer Security Applications Conference (ACSAC). This research project focuses on hidden communication via optical channels. Computers or networks in critical infrastructures are often physically isolated to prevent external access. “Air-gapping” means that these systems have neither wired nor wireless connections to the outside world. Previous attempts to bypass such protection via electromagnetic, acoustic, or optical channels merely work at short distances or low data rates. Moreover, they frequently allow for data exfiltration only, that is, receiving data.
Hidden Optical Channel Uses LEDs in Commercially Available Office Devices
The Intelligent System Security Group of KASTEL – Institute of Information Security and Dependability of KIT, in cooperation with researchers from TU Braunschweig and TU Berlin, have now demonstrated a new attack: With a directed laser beam, an adversary can introduce data into air-gapped systems and retrieve data without additional hardware on-side at the attacked device. “This hidden optical communication uses light-emitting diodes already build into office devices, for instance, to display status messages on printers or telephones,” explains Professor Christian Wressnegger, Head of the Intelligent System Security Group of KASTEL. Light-emitting diodes (LEDs) can receiving light, although they are not designed to do so.
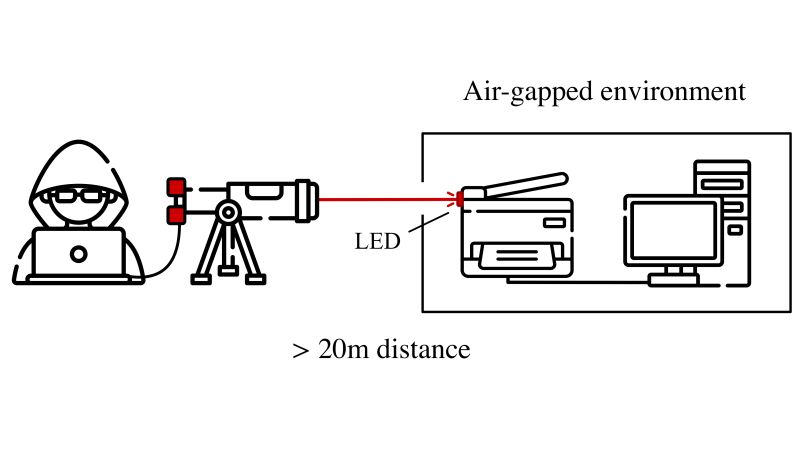
Data Are Transmitted in Both Directions
By directing laser light to already installed LEDs and recording their response, the researchers establish a hidden communication channel over a distance of up to 25 m that can be used bidirectionally (in both directions). It reaches data rates of 18.2 kilobits per second inwards and 100 kilobits per second outwards. This optical attack is possible in commercially available office devices used at companies, universities, and authorities. “The LaserShark project demonstrates how important it is to additionally protect critical IT systems optically next to conventional information and communication technology security measures,” Christian Wressnegger says.
To foster future research on covert communication channels and bridging the air gap, the researchers publish the program code used in their experiments as well as the raw data of their measurements on the LaserShark project website at: https://intellisec.de/research/lasershark.
Research: LaserShark: Establishing Fast, Bidirectional Communication into Air-Gapped Systems


