Internet users leave many traces on websites and online services. Measures such as firewalls, VPN…
INFRASTRUCTURE & TECHNOLOGY
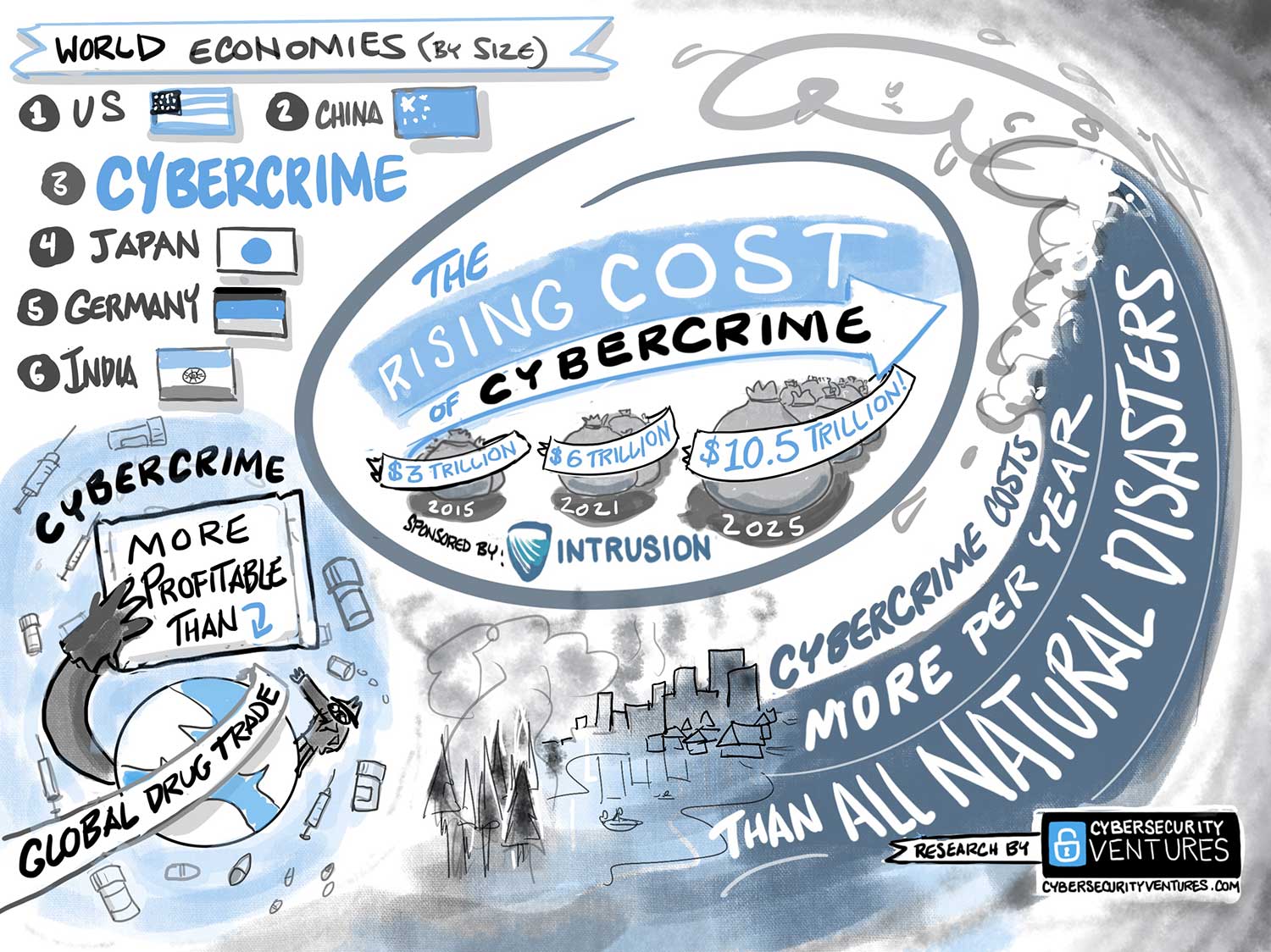
Cyberattacks driven by Artificial Intelligence (AI) pose unprecedented risks to global economies, supply chains, and…
A national advisory referendum on AI could give Congress a clearer signal of the public’s…
The United States could learn from Europe’s approach to incentivizing cybersecurity. Silicon Valley, and the…
Sanctions could prove an effective tool in the fight against spyware abuses. Spyware is a…
Returning end-of-life products to as-new condition is called remanufacturing and can be an essential element…
Ironically, the two countries can look to the past, not the future, for inspiration on…
A review of Lennart Maschmeyer, “Subversion: From Covert Operations to Cyber Conflict” (Oxford University Press,…
With the European Parliament elections now underway, millions of EU citizens are finalizing their decisions…
China Turns to Private Hackers as It Cracks Down on Online Activists on Tiananmen Square Anniversary
Every year ahead of the June 4 commemoration of the Tiananmen Square massacre, the Chinese…